CYBR 171 2023 T1: Lab Exercise 4

Due 04 Jun 11:59pm
Goals
This lab will allow you to practice your Linux skills to penetrate a remote system and give you a bit of a taste of web hacking.
This doesn't feature in the current assignment, but we will have at least one question in the next test related to this lab.
Resources and links
Preparation
We used the Chrome browser and the Chrome extension
Edit My Cookie.
Use Chrome if possible; otherwise, you will need a different method for editing the cookies - there are many.
Summary
- Getting Started:
 Create an account on Gruyere.
Create an account on Gruyere.
- XSS Hacks:
 Demonstrate XSS hacks.
Demonstrate XSS hacks.
- Logging in another user:
 Login as another user without using their password.
Login as another user without using their password.
- Cross-Site Request Forgery (XSRF):
 Add a snippet that deletes snippets.
Add a snippet that deletes snippets.
- Finishing up:
 Submit your answers for the lab to get feedback on what you got right and wrong to help you with the next assignment.
Submit your answers for the lab to get feedback on what you got right and wrong to help you with the next assignment.
- Going Further:
 Want to go further? Check out the resources on PGP.
Want to go further? Check out the resources on PGP.
1. Getting Started
This codelab provided by Google is built around Gruyere /ɡruːˈjɛər/ - a small, cheesy web application that allows its users to publish snippets of text and store assorted files. "Unfortunately," Gruyere has multiple security bugs ranging from cross-site scripting and cross-site request forgery to information disclosure, denial of service, and remote code execution. The goal of this codelab is to guide you through discovering some of these bugs and learning ways to fix them both in Gruyere and in general.
The codelab is organized by types of vulnerabilities. In each section, you'll find a brief description of a vulnerability and a task to find an instance of that vulnerability in Gruyere. Your job is to play the role of a malicious hacker and find and exploit the security bugs.
This video steps through what you need to do to sign up.
Go to
https://google-gruyere.appspot.com/start and sign up for an account for yourself to use when hacking.
Do not use the same password for your Gruyere account as you use for any real service.

Include a screenshot showing that you have signed up for an account.
2. XSS Hacks
You should complete the following XSS hacks
described here.
There are hints and actual instructions on how to carry it out on the page.
Watch this video to get an overview of the exercise, and you may need to review Harith's second web lecture as well because he shows what to do and explains why it works.
Note that unlike in the
Exploit and Fix section, the script to execute is
alert(STUDENT_ID) where you replace
STUDENT_ID with your actual student ID.
Include a screenshot of the hack working to show us that you did actually try this out, and it should include the URL. For example, I would submit the following screenshot when I complete the
File Upload XSS:
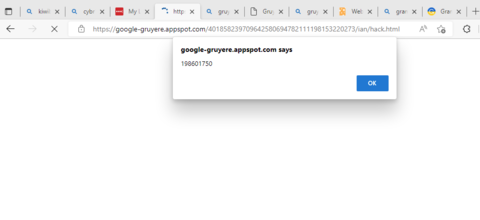

File Upload XSS. This will give you an URL that, when entered into the browser, will execute your script.

Find a reflected XSS attack. Create an URL that, when entered into the browser, will execute your script.

Now find a stored XSS. What we want to do is put a script in a snippet where Gruyere will serve it back to another user.
3. Logging in as another user
You can steal someone else's cookie and use it to login as them.
As for the previous section, document your approach using screenshots.
This video steps through the process.

Create a new user called "victim" with the password "password", and login as this new user.

Steal the cookie associated with "victim" using a XSS attack.

Logout of Gruyere and use
Edit This Cookie to login without knowing victim's password.
3. Cross-Site Request Forgery (XSRF)
If your site is vulnerable to XSS, then the attacker can fake any request as if it came from the user. But even if you've protected against XSS, there's another attack that you need to protect against: cross-site request forgery.
This video steps through the process.

Find a way to get someone to delete one of their Gruyere snippets. Place the code in an existing snippet. Include a screenshot showing the snippet you have added.
4. Finishing up

Submit your answers to these questions using the submission system. In your web browser, go to the top of the Lab 4 page, and click on the
"Submit" link. Make sure that it is a PDF file.
Going Further
Here are some more resources if you want to explore Gruyere and web security further, :
 Create an account on Gruyere.
Create an account on Gruyere.
 Demonstrate XSS hacks.
Demonstrate XSS hacks.
 Login as another user without using their password.
Login as another user without using their password.
 Add a snippet that deletes snippets.
Add a snippet that deletes snippets.
 Submit your answers for the lab to get feedback on what you got right and wrong to help you with the next assignment.
Submit your answers for the lab to get feedback on what you got right and wrong to help you with the next assignment.
 Want to go further? Check out the resources on PGP.
Want to go further? Check out the resources on PGP.

